Useful Tools and Models
This is a collection of different tools, templates, frameworks and articles which have been created to achieve different goals. Over time this will grow as I slowly update and port things over from my old site and my personal store of material I have created. Feel free to use as you see fit the only thing I ask is that you reference me as the original author and drop me a quick email to let me know what you've used and how it has proved useful as this helps me understand reach and utility. Also feel free to drop suggestions about how it could be made better. You can reach me on esa@assureccontrol.com
Security Services Ontology/ERD
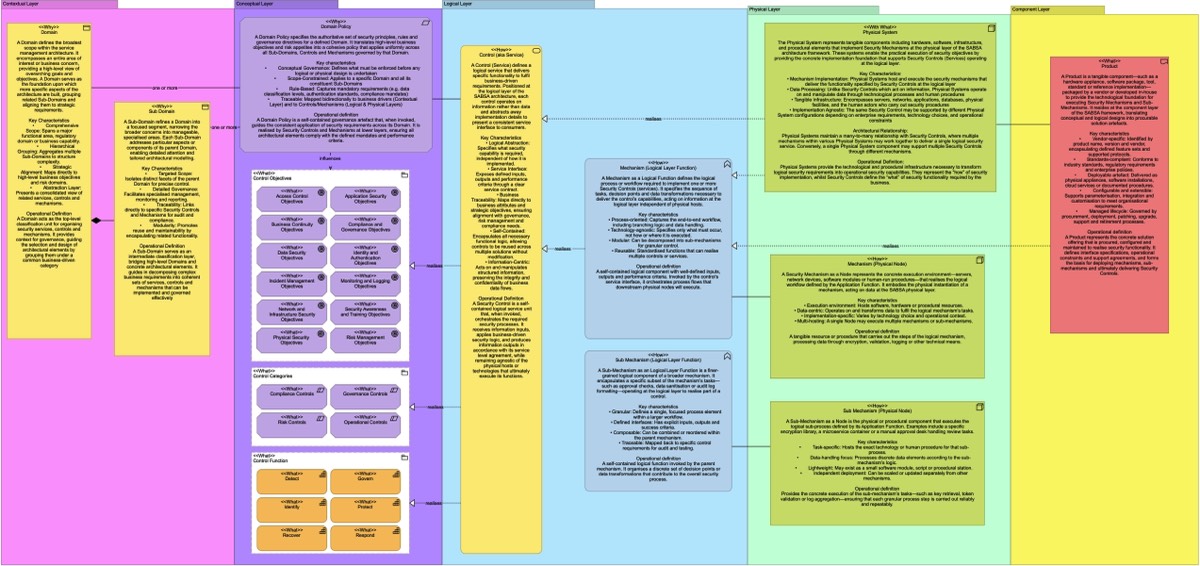
This reference architecture, rooted in the SABSA framework, serves as an ontology or ERD that maps the relationships between business drivers, security domains, controls, and governance processes. Visualising how these elements connect enables a risk-driven approach to security architecture—helping organisations identify gaps, strengthen controls, and align security initiatives with business objectives and compliance requirements.
A presentation which should help you understand and use this framework. Security Services Workshop 25
Security Controls Matrix

This Security Controls Matrix organises key security domains, controls, and business drivers into a cohesive taxonomy. By mapping relationships across layers—ranging from governance and risk to technology and operations—it helps identify gaps, align initiatives with strategic objectives, and drive risk-based security architecture.
Risk Ontology

The “Risk Ontology” presentation introduces a detailed framework for understanding, managing, and mitigating risks within an organisation. By clearly defining critical concepts such as threats, vulnerabilities, controls, and metrics, it provides a structured approach to aligning security measures with business objectives and risk appetite.
The document delves into the relationships between risk elements, such as how threats exploit vulnerabilities to target assets, and outlines the roles of amplifiers, inhibitors, and catalysts in shaping risk scenarios. It also explains the importance of Key Risk Indicators (KRIs), Key Control Indicators (KCIs), and Key Performance Indicators (KPIs) in monitoring, measuring, and improving an organisation’s security posture.
For professionals responsible for risk management, this resource offers insights into building Protection Level Agreements (PLAs), evaluating security maturity, and understanding dependencies that influence risk exposure. This ontology is designed to enhance clarity about risk, which should help your organisation’s ability to anticipate, mitigate, and respond to risks effectively.
Vulnerability Management Frameworks

These framework models provide a holistic approach to cybersecurity and vulnerability management, integrating industry standards, tools, and processes to enhance organisational resilience against cyber threats. It focuses on vulnerability detection and scoring using standards like CVSS and CVE, secure configurations through compliance checks and endpoint hardening, and secure software development via application security testing. It emphasises cyber threat intelligence sharing with protocols like STIX and TAXII and malware analysis through CAPEC and MAEC. The framework also supports incident investigation to refine controls and incorporates industry benchmarks, such as XCCDF, for secure baselines and interoperability. By aligning business processes with technology controls, it reduces attack surfaces, ensures licence compliance, and strengthens software management, creating a robust, standardised defence against evolving cyber risks.
Enterprise or solutions architects leverage this framework to design and implement robust cybersecurity architectures that align with organisational goals and industry best practices. By integrating tools and standards like CVSS, XCCDF, and STIX, they ensure consistent vulnerability management, secure configurations, and streamlined threat intelligence sharing. The framework supports the identification and mitigation of vulnerabilities across software, endpoints, and networks, allowing architects to proactively reduce the attack surface and enhance compliance. It provides structured methodologies for assessing risks, hardening builds, and embedding security into the software development lifecycle through practices like static and dynamic application security testing. Additionally, architects use the framework to facilitate interoperability between security tools and teams, enabling a cohesive, scalable, and efficient cybersecurity strategy tailored to the organisation’s needs.
Threat Intelligence Service Framework

The Threat Intelligence and Predictive Security Framework offers a comprehensive methodology for enhancing an organisation's resilience against cyber threats by integrating threat intelligence, predictive analytics, and collaborative threat mitigation strategies. It emphasises the identification, prioritisation, and proactive management of risks across organisational assets, aligning security investments with current and emerging threat landscapes.
Key Features and Focus Areas:
Threat Intelligence Management:
Facilitates the collection, validation, and dissemination of actionable threat intelligence to improve situational awareness and support security operations.
Incorporates feedback loops, reporting mechanisms, and sharing protocols to ensure intelligence remains relevant and impactful.
Threat Modelling and Risk Prioritisation: * Provides structured frameworks and tools for identifying and assessing threats.
- Utilises methodologies for attack surface mapping, risk scoring, and planning to prioritise remediation efforts effectively.
Predictive Analytics and Behavioural Analysis:
Employs machine learning and behavioural models to forecast potential threats and anomalies.
Supports proactive security measures by identifying attack patterns and high-risk scenarios before they materialise.
Threat Hunting:
Focuses on detecting hidden threats within an organisation’s environment using advanced techniques, such as hypothesis-driven exploration and endpoint threat analysis.
Strengthens defences against advanced persistent threats (APTs) and post-breach indicators.
Adversary Profiling:
- Develops a comprehensive understanding of adversaries’ behaviours, motives, and tactics to refine defensive strategies.
- Leverages intelligence on threat actor activities to enhance situational awareness.
Vulnerability and Exploit Intelligence:
Aggregates and monitors vulnerability information, supporting prioritised remediation activities to reduce risks.
Combines exploit intelligence with proactive defence mechanisms to address high-priority threats.
Threat Sharing and Collaboration:
Promotes cooperative threat intelligence sharing with industry partners, using standards like STIX and TAXII.
Enhances collective defence by fostering cross-organisational communication and coordination.
Strategic Threat Landscape Analysis:
Aligns security investments with long-term strategic goals by evaluating trends and forecasting future threats.
Supports decision-making by mapping risks to business objectives and ensuring readiness for evolving challenges.
Business Value: This framework empowers organisations to preemptively address threats, enhance collaboration, and align cybersecurity initiatives with strategic business objectives. By combining advanced analytics, industry standards, and structured methodologies, it delivers actionable insights, reduces attack surfaces, and establishes a robust defence against the ever-changing threat landscape.
Security architects can use this framework to:
- Align security strategies with business objectives.
- Integrate predictive tools and intelligence-sharing protocols for enhanced situational awareness.
- Proactively identify vulnerabilities and adversary tactics to reduce risks.
- Strengthen resilience against cyber threats by embedding security into operational and strategic planning.
This model provides a scalable, adaptable solution to tackle modern cybersecurity challenges effectively.
Presentations
What Good Looks Like - Metrics

The "What Good Looks Like - Using KPI’s, KCI’s and KRI's Effectively" presentation provides a practical guide for organisations looking to build meaningful and actionable security metrics. Designed with different stakeholder needs in mind—senior leaders, CISOs, and operational teams—it offers a structured approach to measuring and managing security effectiveness.
The framework addresses common challenges, such as focusing too much on technology rather than outcomes, and demonstrates how to align metrics with business priorities and risk management objectives. By breaking down concepts like Key Risk Indicators (KRIs), Key Control Indicators (KCIs), and Key Performance Indicators (KPIs), the presentation helps organisations develop metrics that answer essential questions about risk, control effectiveness, and operational performance.
Whether you’re looking to streamline reporting, improve decision-making, or demonstrate value to the business, this deck provides some tools and insights to get started.
Originally produced in 2021 for presentation at COSAC 21
Herding Cats in a DevSecOps World

The “Herding Cats” presentation offers a clear and structured exploration of how security integrates into modern software development pipelines. It provides an end-to-end view of the DevSecOps lifecycle, from planning and coding to deployment and monitoring, highlighting the importance of constant feedback and security validation throughout.
With practical insights into common security concerns, essential tools, and effective controls, this presentation bridges the gap between traditional security practices and the unique demands of agile development and continuous delivery. It emphasises the importance of tools like Static and Dynamic Application Security Testing (SAST/DAST), Software Composition Analysis (SCA), and Runtime Application Security Protection (RASP), while also addressing critical operational aspects like vulnerability management, dependency checking, and digital trust.
Whether you are a developer, security professional, or organisational leader, this deck will help you understand how to embed security seamlessly into your DevOps processes, enabling you to deliver secure, resilient applications without sacrificing speed or agility.
Originally produced in 2021 for presentation at COSAC 21. This is still relevant but could do with an update to reflect some of the new AI enhanced practices. Its on my to do list.
Business-Driven Cloud Architecture - Discover the Strategic Key to Unlocking Cloud Potential

Dive into "Building Cloud Architectures Top-Down: Aligning with Business Motivations," a presentation that redefines cloud strategy. Unlike traditional, technology-first approaches, this session offers a top-down framework that ensures every cloud initiative is driven by business goals and outcomes.
Learn why many organisations fail to realise the promised benefits of cloud adoption and how aligning with business motivations can bridge this gap. Explore the strengths and limitations of industry frameworks, such as the Microsoft Cloud Reference Architecture, through a lens of business-aligned methodologies like SABSA and POPIT.
Packed with actionable insights, this presentation guides you through understanding business requirements, capability development, and implementing operating models that enable security, efficiency, and innovation. Whether you're embarking on a cloud migration or refining your strategy, this session is your roadmap to a business-driven cloud transformation.
Originally produced in 2024 for presentation at COSAC 24 and presented again at SABSA World London Jan 2025